SAML and API access to Quickbase

|
This topic refers to functionality that is only available to accounts on the Business-level or above plans. If you do not see the functionality described here, either your account or realm has not been configured to show it, or your account is not on one of those plans. |
After you have implemented SAML, programs that use the Quickbase API cannot authenticate using SAML. You must configure the user named in the API_Authenticate call to use Quickbase authentication using one of these three methods:
-
Use user tokens to authenticate instead of API_Authenticate instead of API_Authenticate
API access from a Web browser after user sign-in is possible. Users who have already authenticated (through SAML or Quickbase) can use the API as they normally would.
Override SAML authentication for a user
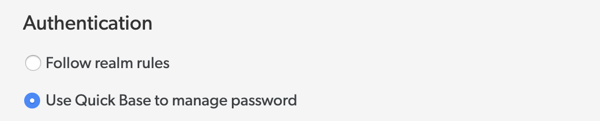
Even if you set up SAML authentication, you can override it on a per-user basis, or create a duplicate user who is allowed to sign in with a Quickbase password. When a user sets this override, a note displays next to the user Realm status level: Approved (password managed by Quickbase).
-
Access the Admin Console and select the Users page.
-
Select the user to override and open the info panel on the right of the page.
-
In the Authentication section, choose Use Quickbase to manage password.
Use user tokens to authenticate instead of API_Authenticate
Users can create their own user tokens in Quickbase by selecting My preferences from the drop-down on the global bar. You can use user tokens to run APIs with permissions.
Many API calls that use an authentication ticket (username and password) can use a parameter called usertoken instead.
Note: Implementing SSO SAML authentication causes any connected sync tables to break if the authentication connection is using username and password. Only a user token authentication allows the connection to resume normal sync updates.
